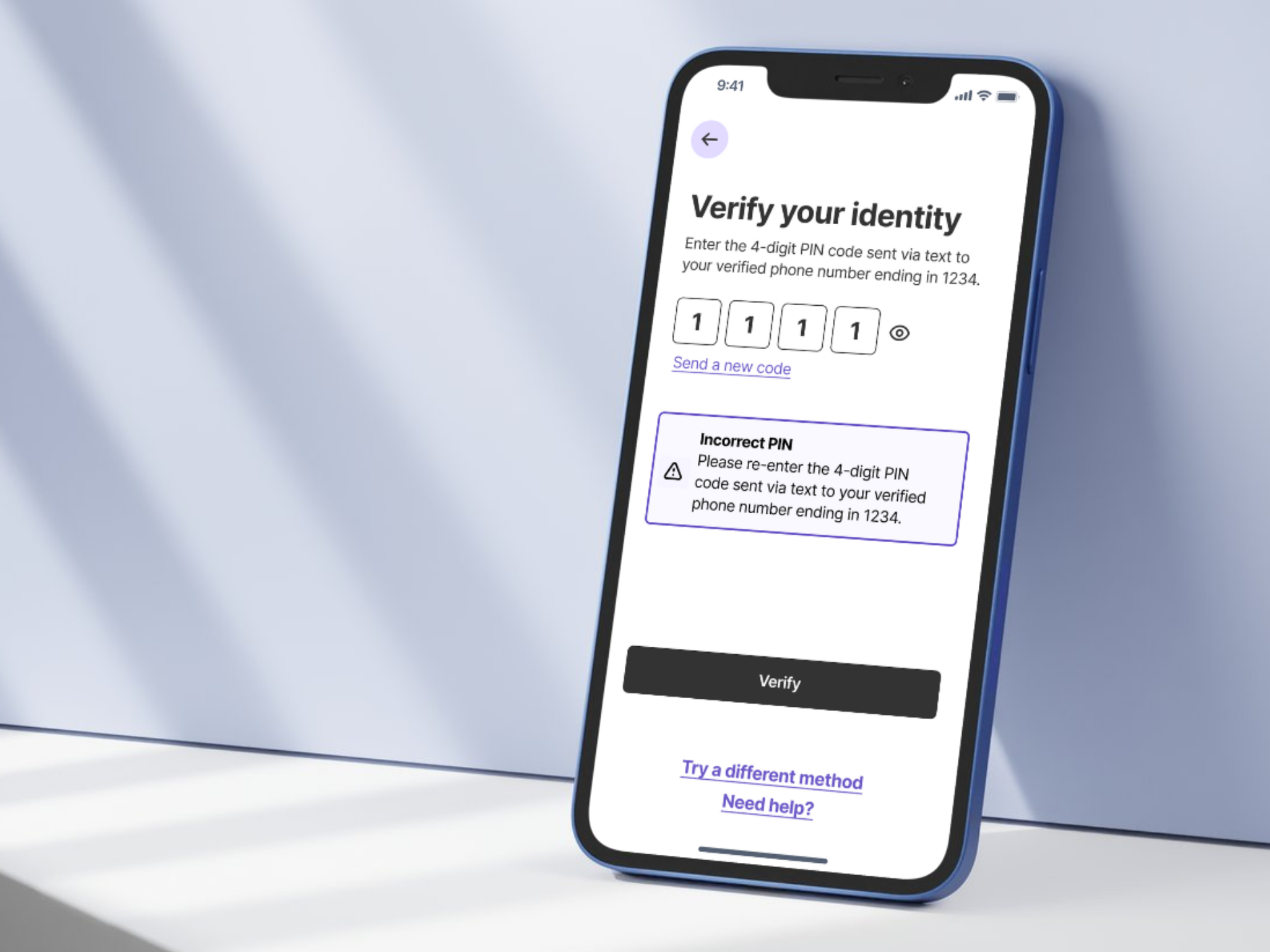
Workshopping Multi-Factor Authentication
UX Research | Interviews | Focus Groups | Accessibility Guidelines
Researching improvements to multi-factor authentication through participatory design and focus groups.
Overview
In this course project, I worked with another researcher and a group of older adult research participants to explore how multi-factor authentication could be improved. Authentication is necessary to access important apps such as banking, investments, healthcare, insurance, and more, but there is a lack of standardization methods across industries.
We envision authentication to be more accessible and efficient for a wider range of users, starting with older adult users.
This project hinged on the participatory design and co-working sessions with our older adult research participants, and it was a wonderful opportunity to use a different approach to research.
Role
UX Designer & Researcher | Focus Group Facilitator
Client
Course Project in Master’s of Human-Computer Interaction
How might we increase usability of authentication methods for older adult users across platforms?
Multi-factor authentication is a non-negotiable for most secure apps such as financial apps, but there is a lack of standardization that results in increased difficulty of use and constant learning.
We identified 12 different methods of authentication, each with subtypes, for a minimum of 22 possible ways to authenticate. This means there is at least 22 possible ways to authenticate which requires different abilities, patterns, devices, behaviors, etc.
Our research explores usability of authentication in two regards:
Accessibility
How easy is it to actually use and access the authentication method considering factors like physical limitations, cognitive decline, familiarity with tech and intuitiveness of the interface?
Tradeoffs
How quickly and smoothly a user can complete the authentication process, particularly in regards to the number of steps required, the need for recall vs recognition, recovery options, and features to save data (stay logged in)?
How did I establish project scope and research questions?
We started with literature reviews to understand the existing landscape. Part of this was finding examples of the types of authentication for clear grouping as we evaluated project scope.
We sent out emails to our older adult co-designers with an introduction and project plan to gauge if our problem statement was relevant to them. Here is some of the feedback we got:
- “It does get confusing, although I don’t generally have a lot of difficulty”
- “I find the auth process annoying for apps that don’t contain sensitive information”
- “I couldn’t authenticate this one time because I lost my phone, and all methods needed it”
Types of Authentication Methods to Include:
- CAPTCHA
- Two Factor Authentication (SMS and App)
- Passkeys (Biometric)
Research Questions to Explore:
- What existing authentication methods are being used most frequently by older adults?
- What kinds of barriers are people facing with these methods?
- What are current workarounds that people use?


How did I address these questions?
We conducted semi-structured interviews with handouts of some commonly used authentication methods to give our participants some context. We discussed their experience, usage, help-seeking behaviors, security, devices used, and activity based preferences for authentication. The interview concluded with an interactive session where participants read CAPTCHAs.
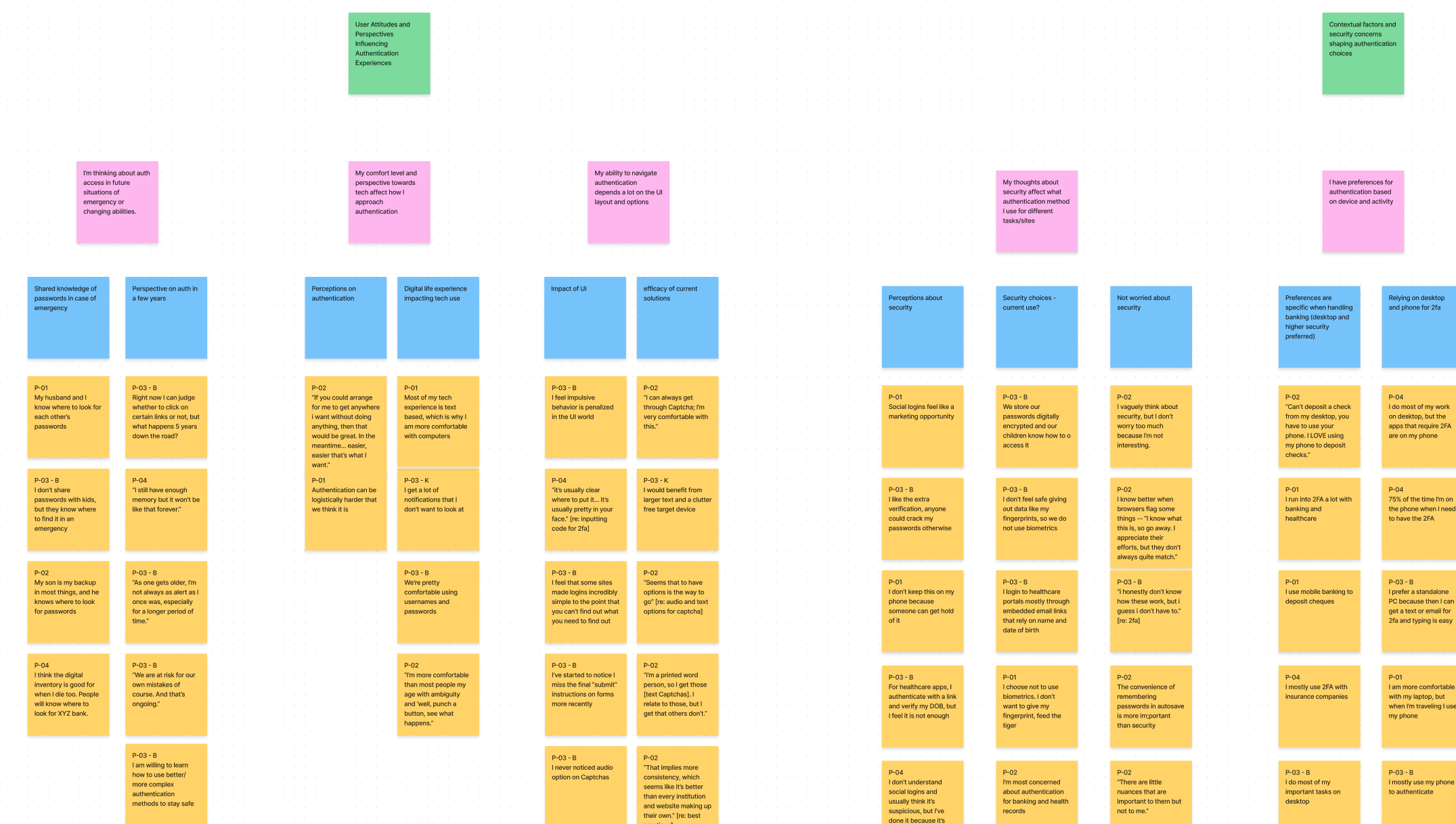
Affinity Diagramming
The interviews provided us with rich data. A few insights below:
- We saw themes of security and support emerge, ideas that we hadn’t initially considered. This broader perspective led us to expand our focus beyond the initial scope of accessibility.
- User preferences for authentication methods varied based on the context, such as the type of activity and device used.
- They had workarounds and envisioned alternative solutions for future scenarios where they might not be able to authenticate.
- Participants highlighted gaps in the support journey when unable to authenticate.
- Passwords and biometrics were used almost daily, and two-factor/captcha happened frequently (weekly or more).
- Troubleshooting looked different for every participant, based on a couple factors:
- Willingness to accept help from other sources
- Human help or digital help
- Available info and instructions within authenticator (forgot password, backup methods, etc)
- Importance and urgency of task
- Authentication wasn’t always accessible for both cognitive and physical needs, but not all users were open to trying a new system for more accessibility (switching from Android to iPhone).
Refining Plans
Our initial ideas focused on the accessibility and efficiency of the most frequent authentication methods. However, our plans started changing based on two emerging themes:
Support Systems
Support for setting up and troubleshooting are vital for all users, but they vary widely.
“There’s no help if you can’t do it. The burden is entirely left to the user.”
“I’m of two minds with the multiple options: why don’t you just give me one that works. But you don’t know which one works.”
Security of Authentication
Users’ perceptions regarding security for tasks, for different authentication methods, and for the tradeoff between security and convenience, affected their willingness to utilize authentication.
“I don’t understand social logins and usually think it’s suspicious, but I’ve done it because it’s easier.”
“I don’t feel safe giving out data like my fingerprints, so we do not use biometrics”
Limitations
At this point in the project, we kept running into two themes below. Due to our project timeline and the need for support from other department areas such as psychology, cybersecurity, and education, we decided to put these topics to the side and hone in on what we could tackle in our remaining time.
Support Systems
Implications of how users perceive security and identity verification when using digital products
Tech Literacy as Part of UX
Widely varying levels of understanding of security methods that impact how people use authentication
Focus Groups with Co-Designer Participants
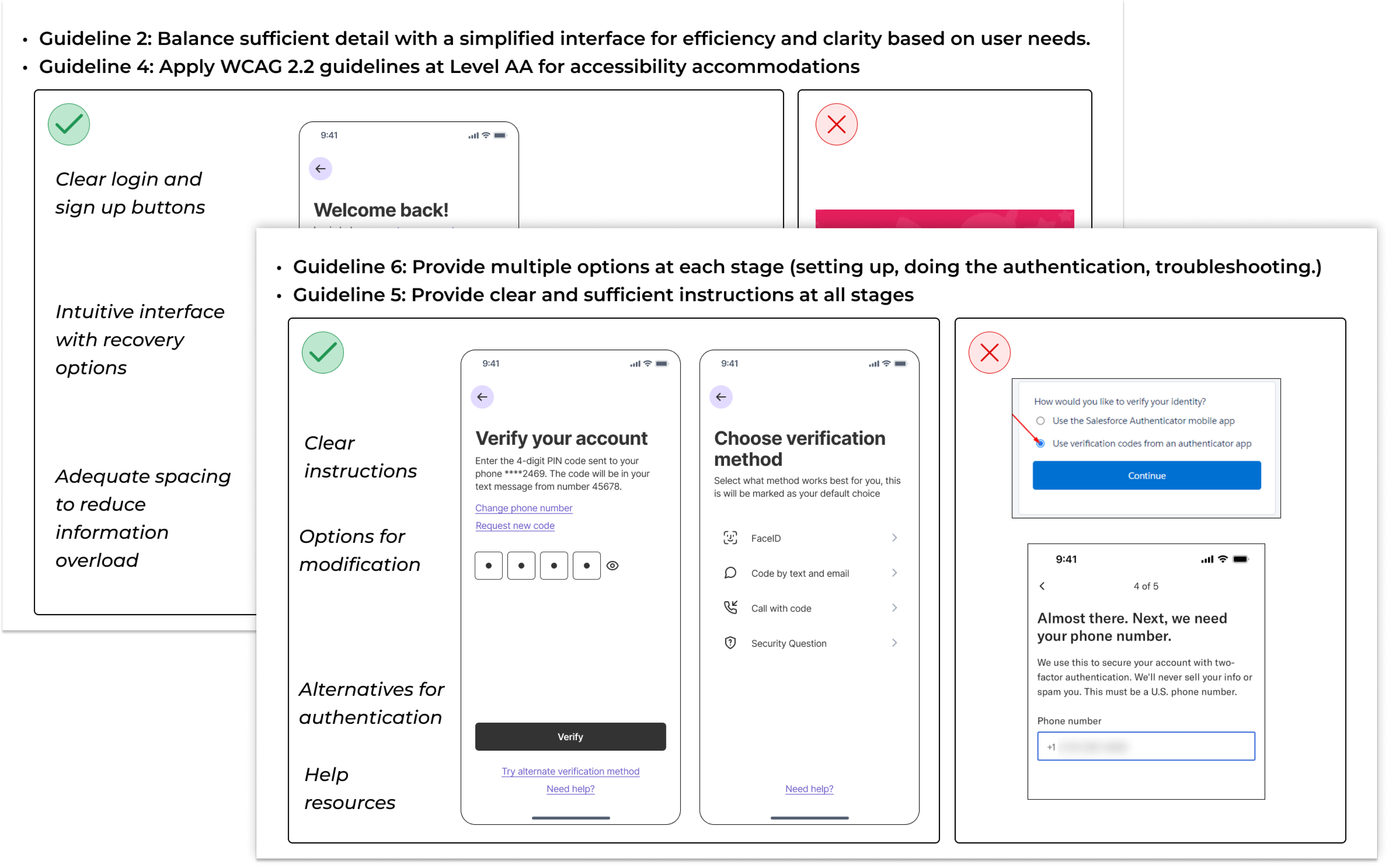
We conducted a semistructured focus group discussion with handouts. Each page of the handout contained the relevant guidelines, our proof of concept screens, and an example that didn’t follow the guidelines.
We wanted to understand how the participants feel about the guidelines in practice, contrasted with screens that do not meet them.
Some key themes we wanted to observe were:
- Balancing simplicity with increased information
- Improving user experience accessibility without sacrificing security
- Preferences for seeking support & troubleshooting throughout different stages of authentication (setup, login, and recovery)
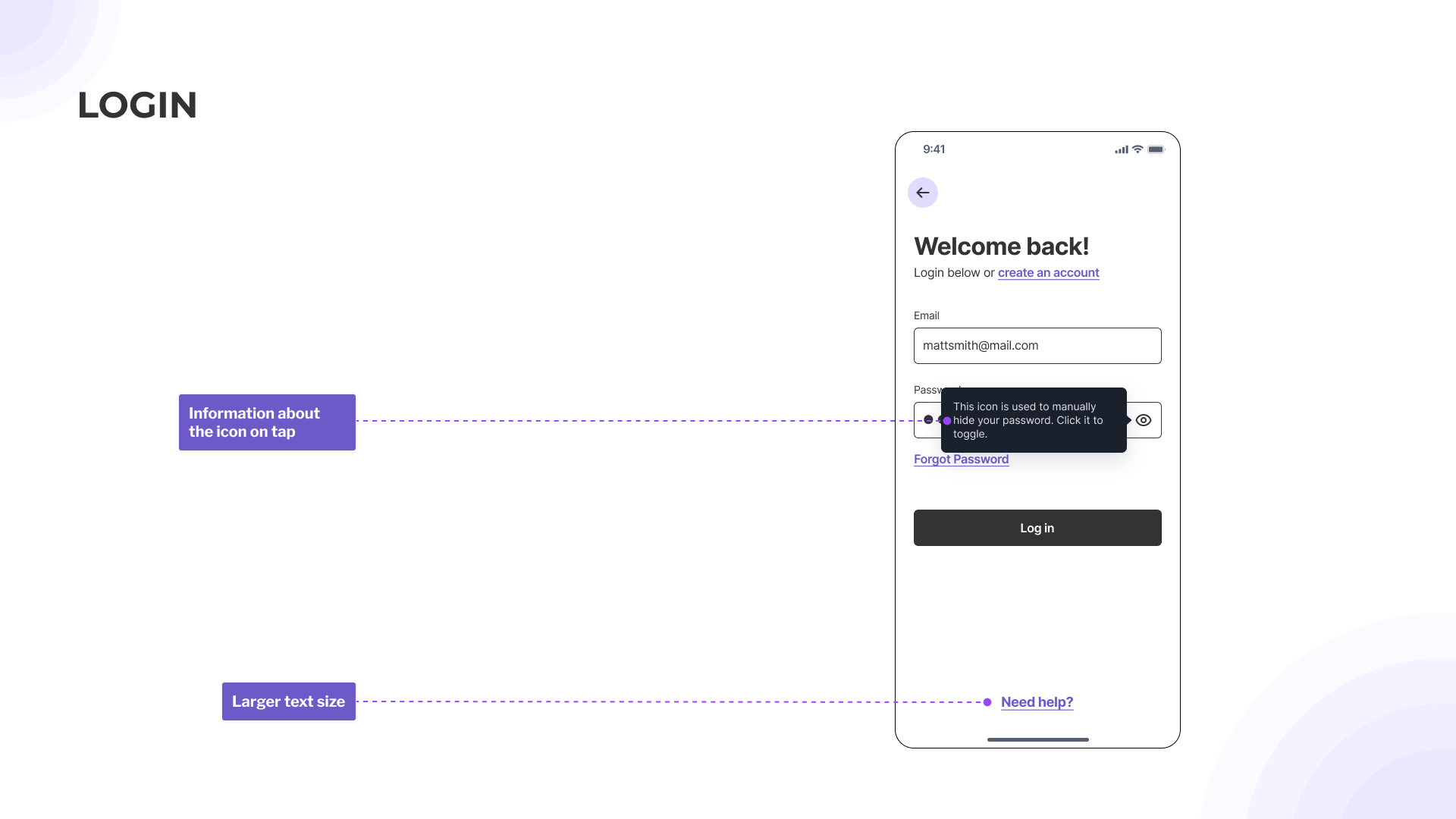
During the focus group, we asked participants to review the screens and provide feedback using sticky notes. The purpose of this activity was to encourage participants to share their input, even if they did not have the opportunity to speak up verbally.
Through this exercise, participants documented numerous comments and observations, covering topics such as icon selection, terminology usage, error handling, and more.
Some of the unexpected feedback that stood out to us at first was:
- The wide range of interpretations for icons and terminology
- The importance of UX writing
- Preference for micro-interactions to display information

How did I establish key insights and themes?
We produced a comprehensive list of findings, but I am only including the two main themes below for brevity.
Theme 1: Support Systems
“There’s no help if you can’t do it. The burden is entirely left to the user.”
“I’m of two minds with the multiple options: why don’t you just give me one that works. But you don’t know which one works.”
“It’s not easy for me to get tech support over the phone.”
- The interviews revealed that support was a significant area of focus for the participants.
- This included support for setting up the account and troubleshooting when unable to authenticate.
- Troubleshooting looked different for every participant, based on a couple factors:
- Willingness to accept help from other sources.
- Human help or digital help.
- Available info and instructions within authenticator (forgot password, backup methods, etc)
- Importance and urgency of task.
Theme 2: Clarity & Accessibility
“I’m not colorblind, but the colors can be difficult.”
“I think it’s reasonable that older adults want to know what happens when they press a button.”
“Authentication can be logistically harder that we think it is.”
- We observed that the wide variety of methods and lack of standardization can lead to confusion and frustration for users.
- Key insights we got from the session:
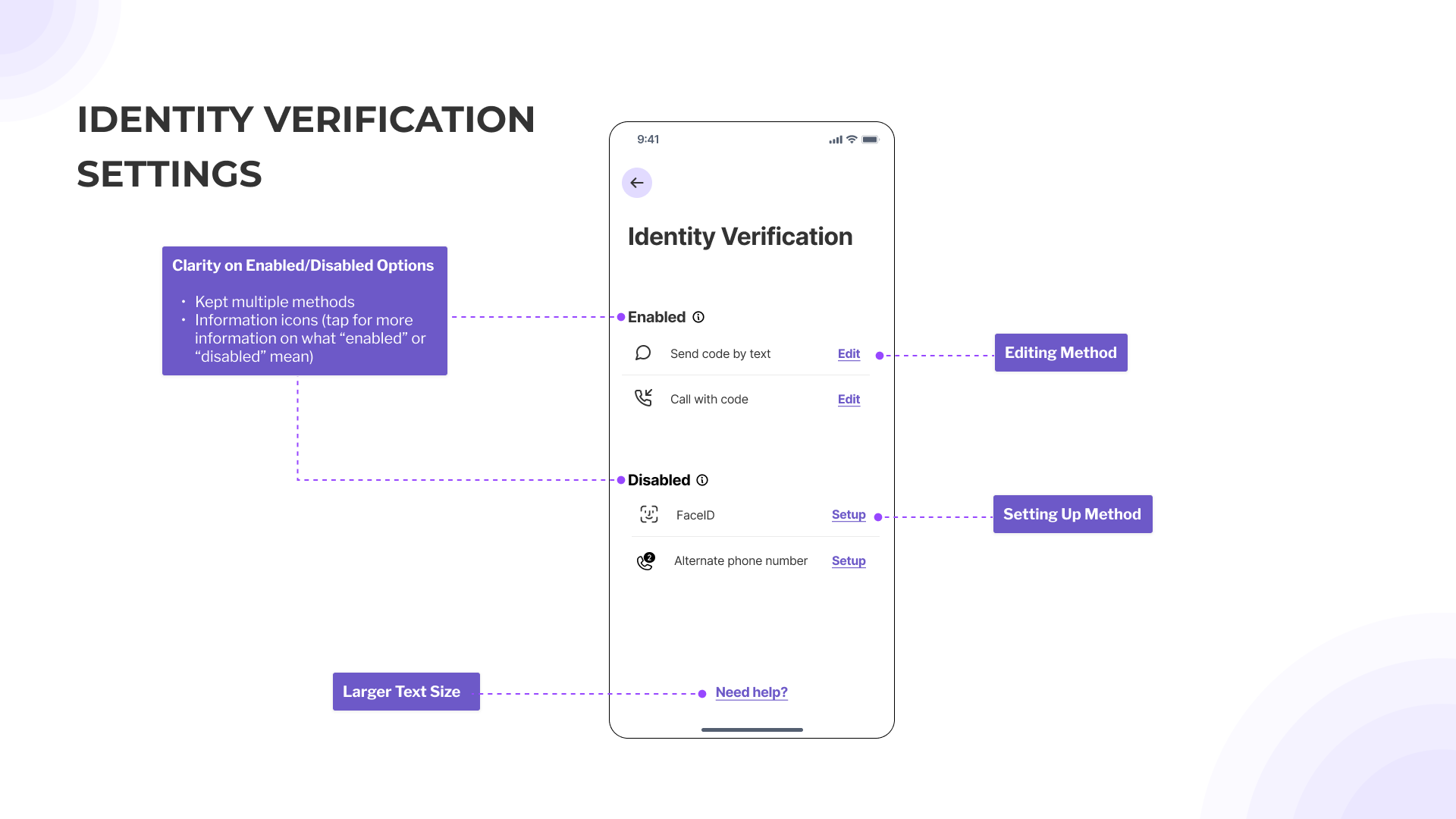
- Make cognitively accessible screens by following clear terminology and language, starting with an action verb, autofill etc
- Icons were helpful but needed additional information to understand what they mean
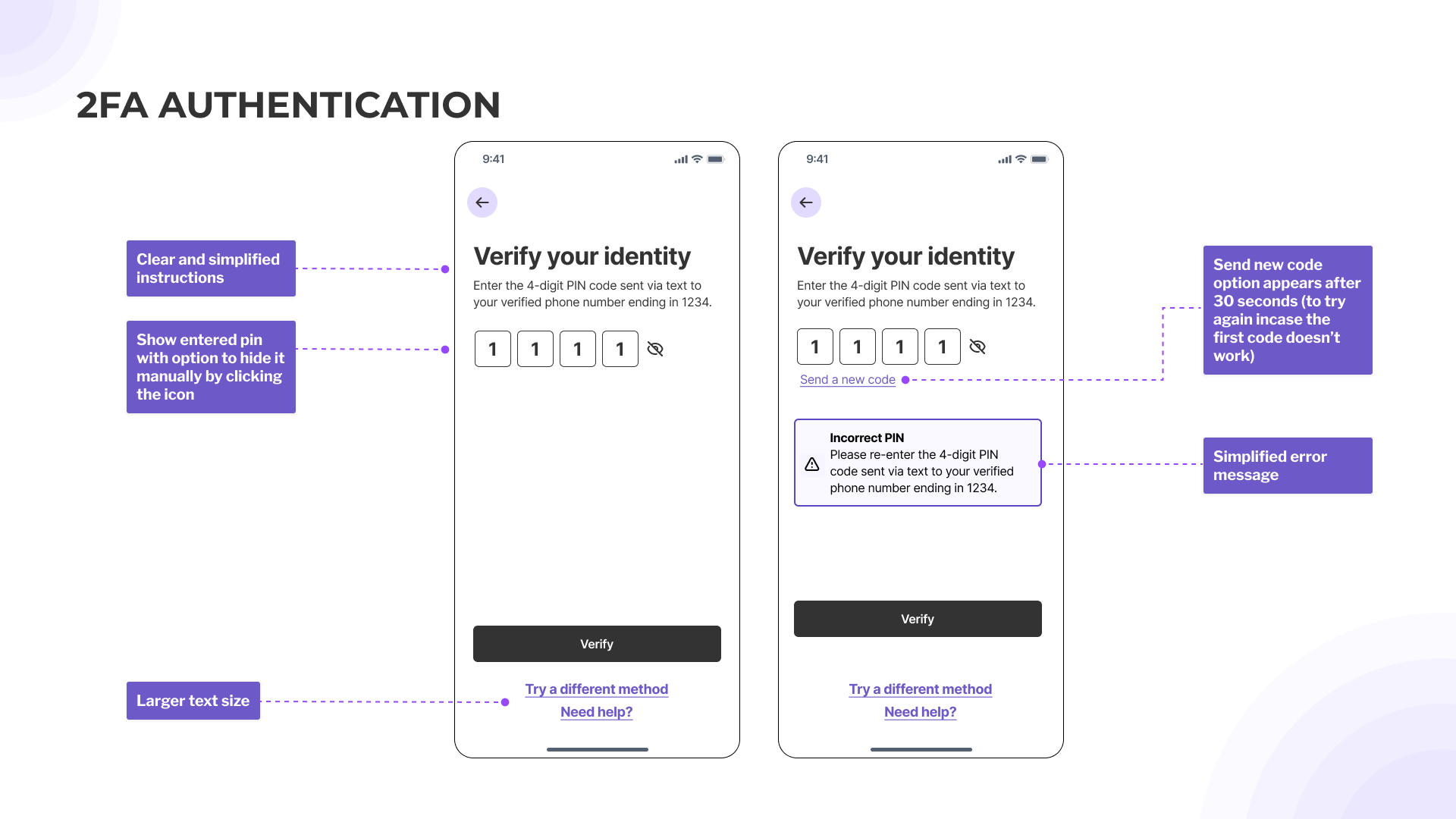
- Provide larger text sizing for action buttons while maintaining spacing
- Provide hover interactions for information rather than overloading the page with potentially unnecessary information (only needed in specific instances)
How did I apply these insights to design?
Based on the insights, we created a set of guidelines for best practices while designing authentication along with a proof of concept:
Guidelines
- Provide clear and actionable feedback in case of errors.
- Balance sufficient detail with a simplified interface for efficiency and clarity based on user needs.
- Enable easier recovery options and allow room for user errors to prevent a sense of penalty.
- Apply WCAG 2.2 guidelines at Level AA for accessibility accommodations.
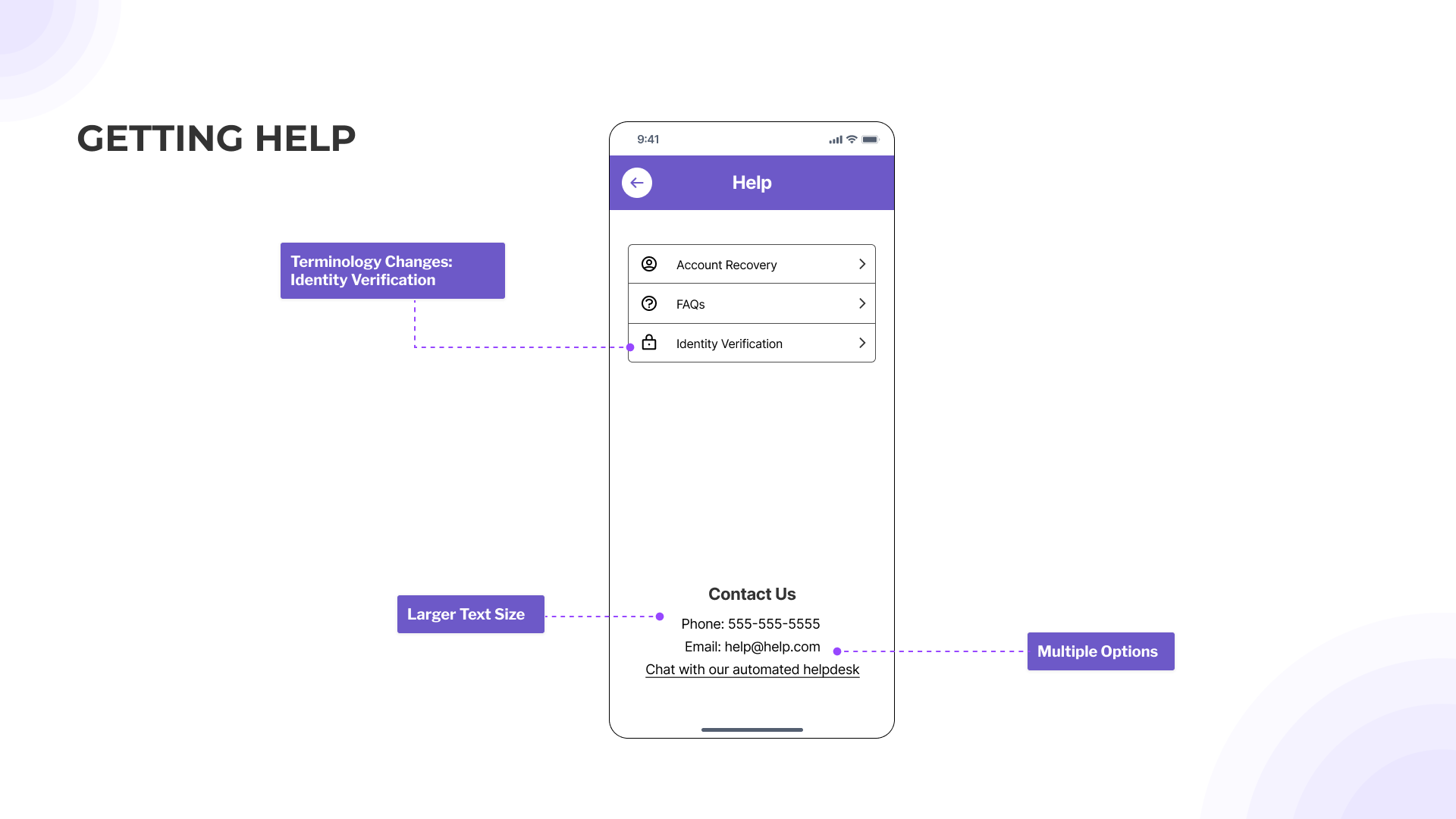
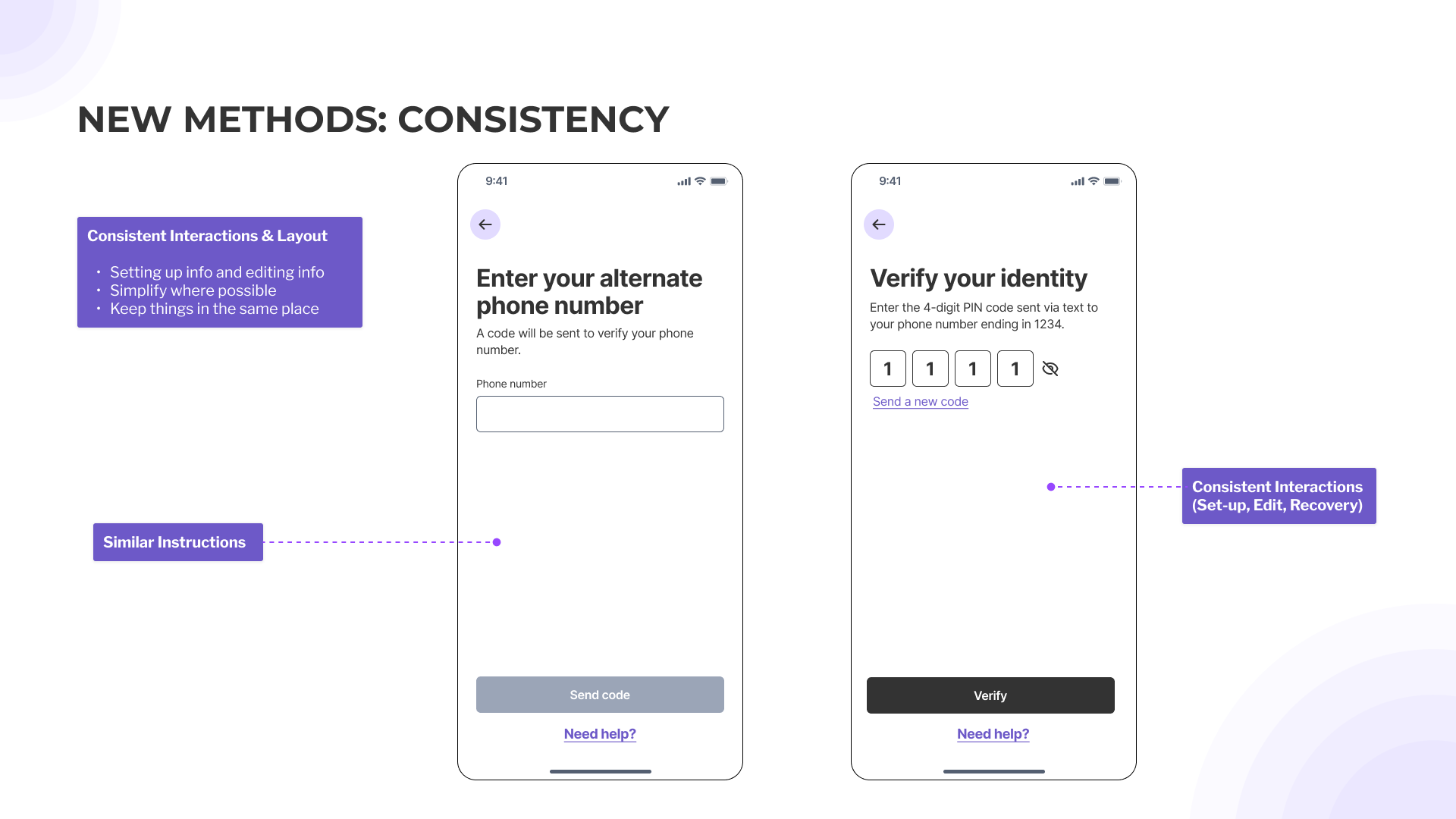
- Provide clear and sufficient instructions at all stages.
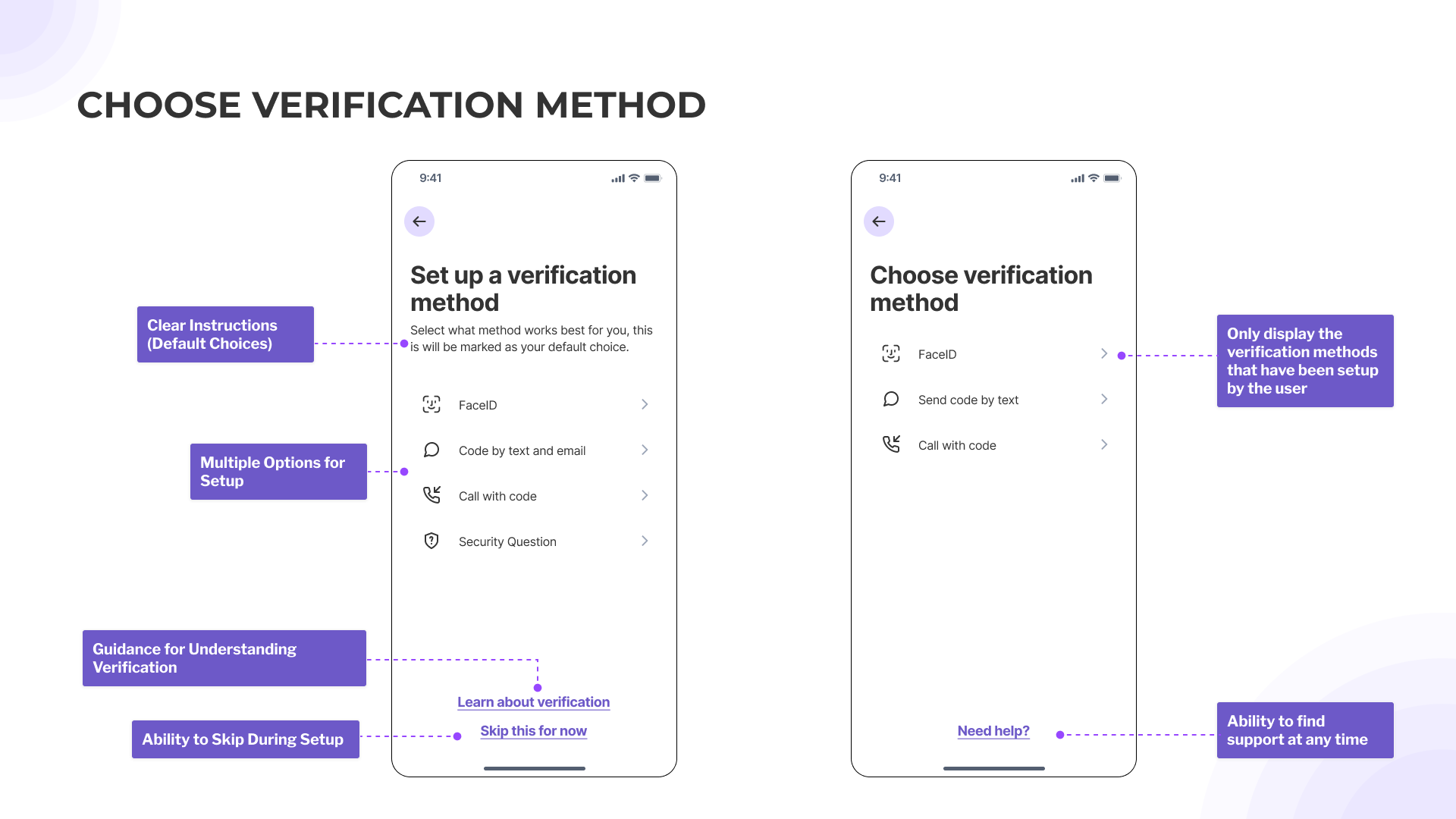
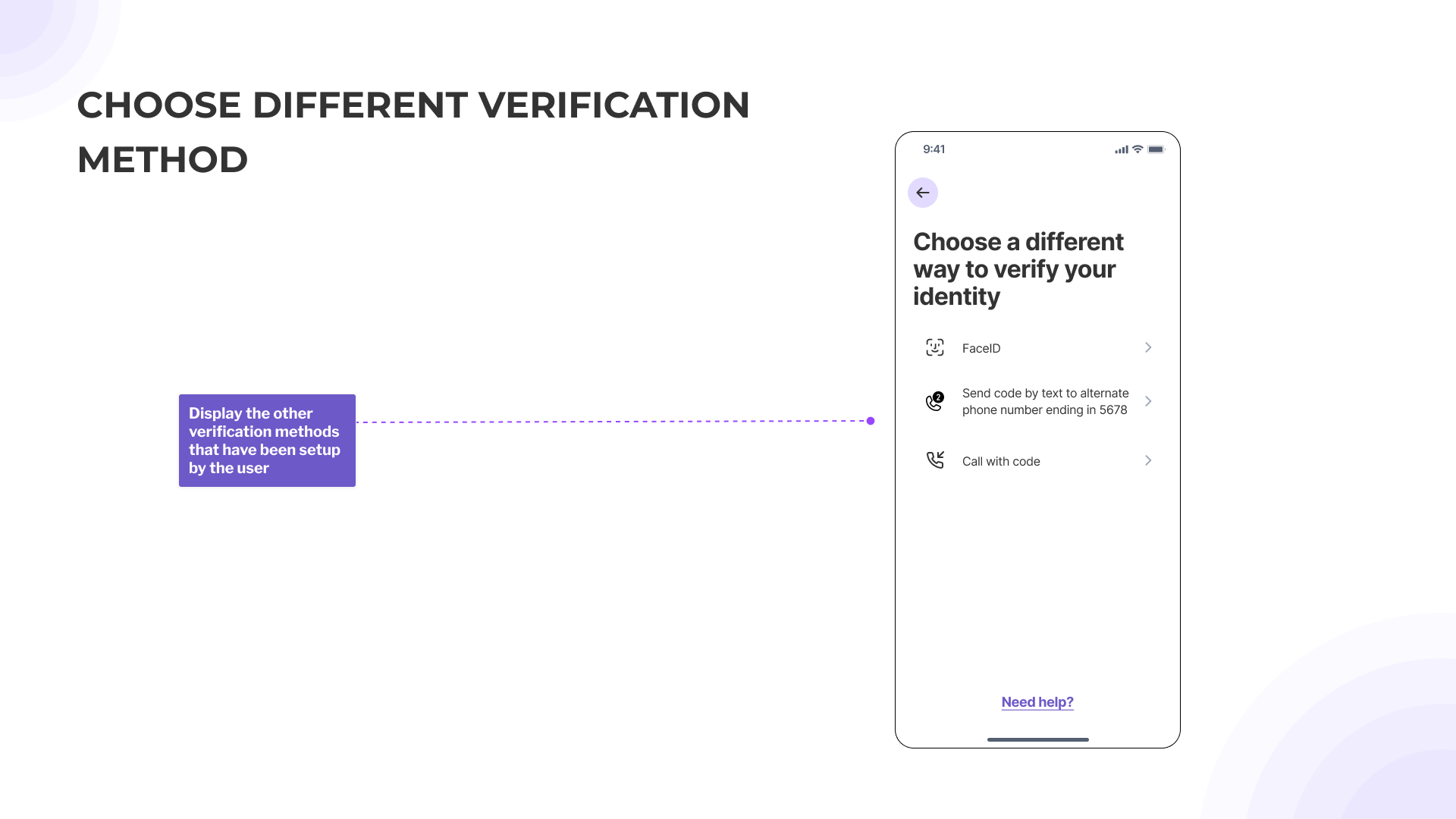
- Provide multiple options at each stage (setting up, doing the authentication, troubleshooting).
- Consider the changing abilities and needs of older adult users in terms of both accessibility and functionality.
Reflection on Participatory Design with Older Adult Co-Designers
The Diversity of “Older Adults”
Products for “older adults aged 60-90” is an incredibly diverse range, but they tend to treat them as a monolith.
We’ll work on:
- Intentionally narrowing our target user audience by multiple factors (going beyond age range alone)
- Considering different elements of ability such as digital life experience
“With”, Not “For”
Products built on assumptions probably aren’t solving any problems (and might make new issues).
We’ll work on:
- Addressing our own assumptions when we build digital products
- Starting with research & advocating for participatory design
Digital Ageism & Societal Ageism
Digital products have a direct impact on how people are perceived in the real world.
We’ll work on:
- Making age-diversity a starting factor in design, not a last minute check-box
- Considering the implications of tech usage beyond the screen
Workshopping Multi-Factor Authentication
UX Research | Interviews | Focus Groups | Accessibility Guidelines
Researching improvements to multi-factor authentication through participatory design and focus groups.

Overview
In this course project, I worked with another researcher and a group of older adult research participants to explore how multi-factor authentication could be improved. Authentication is necessary to access important apps such as banking, investments, healthcare, insurance, and more, but there is a lack of standardization methods across industries.
We envision authentication to be more accessible and efficient for a wider range of users, starting with older adult users.
This project hinged on the participatory design and co-working sessions with our older adult research participants, and it was a wonderful opportunity to use a different approach to research.
Role
UX Designer & Researcher | Focus Group Facilitator
Client
Course Project in Master’s of Human-Computer Interaction
How might we increase usability of authentication methods for older adult users across platforms?
Multi-factor authentication is a non-negotiable for most secure apps such as financial apps, but there is a lack of standardization that results in increased difficulty of use and constant learning.
We identified 12 different methods of authentication, each with subtypes, for a minimum of 22 possible ways to authenticate. This means there is at least 22 possible ways to authenticate which requires different abilities, patterns, devices, behaviors, etc.
Our research explores usability of authentication in two regards:
Accessibility
How easy is it to actually use and access the authentication method considering factors like physical limitations, cognitive decline, familiarity with tech and intuitiveness of the interface?
Tradeoffs
How quickly and smoothly a user can complete the authentication process, particularly in regards to the number of steps required, the need for recall vs recognition, recovery options, and features to save data (stay logged in)?
How did I establish project scope and research questions?
We started with literature reviews to understand the existing landscape. Part of this was finding examples of the types of authentication for clear grouping as we evaluated project scope.
We sent out emails to our older adult co-designers with an introduction and project plan to gauge if our problem statement was relevant to them. Here is some of the feedback we got:
- “It does get confusing, although I don’t generally have a lot of difficulty”
- “I find the auth process annoying for apps that don’t contain sensitive information”
- “I couldn’t authenticate this one time because I lost my phone, and all methods needed it”
Types of Authentication Methods to Include:
- CAPTCHA
- Two Factor Authentication (SMS and App)
- Passkeys (Biometric)
Research Questions to Explore:
- What existing authentication methods are being used most frequently by older adults?
- What kinds of barriers are people facing with these methods?
- What are current workarounds that people use?


How did I address these questions?
We conducted semi-structured interviews with handouts of some commonly used authentication methods to give our participants some context. We discussed their experience, usage, help-seeking behaviors, security, devices used, and activity based preferences for authentication. The interview concluded with an interactive session where participants read CAPTCHAs.
Affinity Diagramming
The interviews provided us with rich data. A few insights below:
- We saw themes of security and support emerge, ideas that we hadn’t initially considered. This broader perspective led us to expand our focus beyond the initial scope of accessibility.
- User preferences for authentication methods varied based on the context, such as the type of activity and device used.
- They had workarounds and envisioned alternative solutions for future scenarios where they might not be able to authenticate.
- Participants highlighted gaps in the support journey when unable to authenticate.
- Passwords and biometrics were used almost daily, and two-factor/captcha happened frequently (weekly or more).
- Troubleshooting looked different for every participant, based on a couple factors:
- Willingness to accept help from other sources
- Human help or digital help
- Available info and instructions within authenticator (forgot password, backup methods, etc)
- Importance and urgency of task
- Authentication wasn’t always accessible for both cognitive and physical needs, but not all users were open to trying a new system for more accessibility (switching from Android to iPhone).

Refining Plans
Our initial ideas focused on the accessibility and efficiency of the most frequent authentication methods. However, our plans started changing based on two emerging themes:
Support Systems
Support for setting up and troubleshooting are vital for all users, but they vary widely.
“There’s no help if you can’t do it. The burden is entirely left to the user.”
“I’m of two minds with the multiple options: why don’t you just give me one that works. But you don’t know which one works.”
Security of Authentication
Users’ perceptions regarding security for tasks, for different authentication methods, and for the tradeoff between security and convenience, affected their willingness to utilize authentication.
“I don’t understand social logins and usually think it’s suspicious, but I’ve done it because it’s easier.”
“I don’t feel safe giving out data like my fingerprints, so we do not use biometrics”
Limitations
At this point in the project, we kept running into two themes below. Due to our project timeline and the need for support from other department areas such as psychology, cybersecurity, and education, we decided to put these topics to the side and hone in on what we could tackle in our remaining time.
Support Systems
Implications of how users perceive security and identity verification when using digital products
Tech Literacy as Part of UX
Widely varying levels of understanding of security methods that impact how people use authentication
Focus Groups with Co-Designer Participants
We conducted a semistructured focus group discussion with handouts. Each page of the handout contained the relevant guidelines, our proof of concept screens, and an example that didn’t follow the guidelines.
We wanted to understand how the participants feel about the guidelines in practice, contrasted with screens that do not meet them.
Some key themes we wanted to observe were:
- Balancing simplicity with increased information
- Improving user experience accessibility without sacrificing security
- Preferences for seeking support & troubleshooting throughout different stages of authentication (setup, login, and recovery)

During the focus group, we asked participants to review the screens and provide feedback using sticky notes. The purpose of this activity was to encourage participants to share their input, even if they did not have the opportunity to speak up verbally.
Through this exercise, participants documented numerous comments and observations, covering topics such as icon selection, terminology usage, error handling, and more.
Some of the unexpected feedback that stood out to us at first was:
- The wide range of interpretations for icons and terminology
- The importance of UX writing
- Preference for micro-interactions to display information

How did I establish key insights and themes?
We produced a comprehensive list of findings, but I am only including the two main themes below for brevity.
Theme 1: Support Systems
“There’s no help if you can’t do it. The burden is entirely left to the user.”
“I’m of two minds with the multiple options: why don’t you just give me one that works. But you don’t know which one works.”
“It’s not easy for me to get tech support over the phone.”
- The interviews revealed that support was a significant area of focus for the participants.
- This included support for setting up the account and troubleshooting when unable to authenticate.
- Troubleshooting looked different for every participant, based on a couple factors:
- Willingness to accept help from other sources.
- Human help or digital help.
- Available info and instructions within authenticator (forgot password, backup methods, etc)
- Importance and urgency of task.
Theme 2: Clarity & Accessibility
“I’m not colorblind, but the colors can be difficult.”
“I think it’s reasonable that older adults want to know what happens when they press a button.”
“Authentication can be logistically harder that we think it is.”
- We observed that the wide variety of methods and lack of standardization can lead to confusion and frustration for users.
- Key insights we got from the session:
- Make cognitively accessible screens by following clear terminology and language, starting with an action verb, autofill etc
- Icons were helpful but needed additional information to understand what they mean
- Provide larger text sizing for action buttons while maintaining spacing
- Provide hover interactions for information rather than overloading the page with potentially unnecessary information (only needed in specific instances)
How did I apply these insights to design?
Based on the insights, we created a set of guidelines for best practices while designing authentication along with a proof of concept:
Guidelines
- Provide clear and actionable feedback in case of errors.
- Balance sufficient detail with a simplified interface for efficiency and clarity based on user needs.
- Enable easier recovery options and allow room for user errors to prevent a sense of penalty.
- Apply WCAG 2.2 guidelines at Level AA for accessibility accommodations.
- Provide clear and sufficient instructions at all stages.
- Provide multiple options at each stage (setting up, doing the authentication, troubleshooting).
- Consider the changing abilities and needs of older adult users in terms of both accessibility and functionality.








Reflection on Participatory Design with Older Adult Co-Designers
The Diversity of “Older Adults”
Products for “older adults aged 60-90” is an incredibly diverse range, but they tend to treat them as a monolith.
We’ll work on:
- Intentionally narrowing our target user audience by multiple factors (going beyond age range alone)
- Considering different elements of ability such as digital life experience
“With”, Not “For”
Products built on assumptions probably aren’t solving any problems (and might make new issues).
We’ll work on:
- Addressing our own assumptions when we build digital products
- Starting with research & advocating for participatory design
Digital Ageism & Societal Ageism
Digital products have a direct impact on how people are perceived in the real world.
We’ll work on:
- Making age-diversity a starting factor in design, not a last minute check-box
- Considering the implications of tech usage beyond the screen
Workshopping Multi-Factor Authentication
UX Research | Interviews | Focus Groups | Accessibility Guidelines
Researching improvements to multi-factor authentication through participatory design and focus groups.

Overview
In this course project, I worked with another researcher and a group of older adult research participants to explore how multi-factor authentication could be improved. Authentication is necessary to access important apps such as banking, investments, healthcare, insurance, and more, but there is a lack of standardization methods across industries.
We envision authentication to be more accessible and efficient for a wider range of users, starting with older adult users.
This project hinged on the participatory design and co-working sessions with our older adult research participants, and it was a wonderful opportunity to use a different approach to research.
Role
UX Designer & Researcher | Focus Group Facilitator
Client
Course Project in Master’s of Human-Computer Interaction
How might we increase usability of authentication methods for older adult users across platforms?
Multi-factor authentication is a non-negotiable for most secure apps such as financial apps, but there is a lack of standardization that results in increased difficulty of use and constant learning.
We identified 12 different methods of authentication, each with subtypes, for a minimum of 22 possible ways to authenticate. This means there is at least 22 possible ways to authenticate which requires different abilities, patterns, devices, behaviors, etc.
Our research explores usability of authentication in two regards:
Accessibility
How easy is it to actually use and access the authentication method considering factors like physical limitations, cognitive decline, familiarity with tech and intuitiveness of the interface?
Efficiency
How quickly and smoothly a user can complete the authentication process, particularly in regards to the number of steps required, the need for recall vs recognition, recovery options, and features to save data (stay logged in)?
How did I establish project scope and research questions?
We started with literature reviews to understand the existing landscape. Part of this was finding examples of the types of authentication for clear grouping as we evaluated project scope.
We sent out emails to our older adult co-designers with an introduction and project plan to gauge if our problem statement was relevant to them. Here is some of the feedback we got:
- “It does get confusing, although I don’t generally have a lot of difficulty”
- “I find the auth process annoying for apps that don’t contain sensitive information”
- “I couldn’t authenticate this one time because I lost my phone, and all methods needed it”
Types of Authentication Methods to Include:
- CAPTCHA
- Two Factor Authentication (SMS and App)
- Passkeys (Biometric)
Research Questions to Explore:
- What existing authentication methods are being used most frequently by older adults?
- What kinds of barriers are people facing with these methods?
- What are current workarounds that people use?


How did I address these questions?
We conducted semi-structured interviews with handouts of some commonly used authentication methods to give our participants some context. We discussed their experience, usage, help-seeking behaviors, security, devices used, and activity based preferences for authentication. The interview concluded with an interactive session where participants read CAPTCHAs.
Affinity Diagramming
The interviews provided us with rich data. A few insights below:
- We saw themes of security and support emerge, ideas that we hadn’t initially considered. This broader perspective led us to expand our focus beyond the initial scope of accessibility.
- User preferences for authentication methods varied based on the context, such as the type of activity and device used.
- They had workarounds and envisioned alternative solutions for future scenarios where they might not be able to authenticate.
- Participants highlighted gaps in the support journey when unable to authenticate.
- Passwords and biometrics were used almost daily, and two-factor/captcha happened frequently (weekly or more).
- Troubleshooting looked different for every participant, based on a couple factors:
- Willingness to accept help from other sources
- Human help or digital help
- Available info and instructions within authenticator (forgot password, backup methods, etc)
- Importance and urgency of task
- Authentication wasn’t always accessible for both cognitive and physical needs, but not all users were open to trying a new system for more accessibility (switching from Android to iPhone).

Refining Plans
Our initial ideas focused on the accessibility and efficiency of the most frequent authentication methods. However, our plans started changing based on two emerging themes:
Support Systems
Support for setting up and troubleshooting are vital for all users, but they vary widely.
“There’s no help if you can’t do it. The burden is entirely left to the user.”
“I’m of two minds with the multiple options: why don’t you just give me one that works. But you don’t know which one works.”
Security of Authentication
Users’ perceptions regarding security for tasks, for different authentication methods, and for the tradeoff between security and convenience, affected their willingness to utilize authentication.
“I don’t understand social logins and usually think it’s suspicious, but I’ve done it because it’s easier.”
“I don’t feel safe giving out data like my fingerprints, so we do not use biometrics”
Limitations
At this point in the project, we kept running into two themes below. Due to our project timeline and the need for support from other department areas such as psychology, cybersecurity, and education, we decided to put these topics to the side and hone in on what we could tackle in our remaining time.
Perceptions of Security
Implications of how users perceive security and identity verification when using digital products
Tech Literacy as Part of UX
Widely varying levels of understanding of security methods that impact how people use authentication
Focus Groups with Co-Designer Participants
We conducted a semistructured focus group discussion with handouts. Each page of the handout contained the relevant guidelines, our proof of concept screens, and an example that didn’t follow the guidelines.
We wanted to understand how the participants feel about the guidelines in practice, contrasted with screens that do not meet them.
Some key themes we wanted to observe were:
- Balancing simplicity with increased information
- Improving user experience accessibility without sacrificing security
- Preferences for seeking support & troubleshooting throughout different stages of authentication (setup, login, and recovery)


During the focus group, we asked participants to review the screens and provide feedback using sticky notes. The purpose of this activity was to encourage participants to share their input, even if they did not have the opportunity to speak up verbally.
Through this exercise, participants documented numerous comments and observations, covering topics such as icon selection, terminology usage, error handling, and more.
Some of the unexpected feedback that stood out to us at first was:
- The wide range of interpretations for icons and terminology
- The importance of UX writing
- Preference for micro-interactions to display information
How did I establish key insights and themes?
We produced a comprehensive list of findings, but I am only including the two main themes below for brevity.
Theme 1: Support Systems
“There’s no help if you can’t do it. The burden is entirely left to the user.”
“I’m of two minds with the multiple options: why don’t you just give me one that works. But you don’t know which one works.”
“It’s not easy for me to get tech support over the phone.”
- The interviews revealed that support was a significant area of focus for the participants.
- This included support for setting up the account and troubleshooting when unable to authenticate.
- Troubleshooting looked different for every participant, based on a couple factors:
- Willingness to accept help from other sources.
- Human help or digital help.
- Available info and instructions within authenticator (forgot password, backup methods, etc)
- Importance and urgency of task.
Theme 2: Clarity & Accessibility
“I’m not colorblind, but the colors can be difficult.”
“I think it’s reasonable that older adults want to know what happens when they press a button.”
“Authentication can be logistically harder that we think it is.”
- We observed that the wide variety of methods and lack of standardization can lead to confusion and frustration for users.
- Key insights we got from the session:
- Make cognitively accessible screens by following clear terminology and language, starting with an action verb, autofill etc
- Icons were helpful but needed additional information to understand what they mean
- Provide larger text sizing for action buttons while maintaining spacing
- Provide hover interactions for information rather than overloading the page with potentially unnecessary information (only needed in specific instances)
How did I apply these insights to design?
Based on the insights, we created a set of guidelines for best practices while designing authentication along with a proof of concept:
Guidelines
- Provide clear and actionable feedback in case of errors.
- Balance sufficient detail with a simplified interface for efficiency and clarity based on user needs.
- Enable easier recovery options and allow room for user errors to prevent a sense of penalty.
- Apply WCAG 2.2 guidelines at Level AA for accessibility accommodations.
- Provide clear and sufficient instructions at all stages.
- Provide multiple options at each stage (setting up, doing the authentication, troubleshooting).
- Consider the changing abilities and needs of older adult users in terms of both accessibility and functionality.








Reflection on Participatory Design with Older Adult Co-Designers
The Diversity of “Older Adults”
Products for “older adults aged 60-90” is an incredibly diverse range, but they tend to treat them as a monolith.
We’ll work on:
- Intentionally narrowing our target user audience by multiple factors (going beyond age range alone)
- Considering different elements of ability such as digital life experience
“With”, Not “For”
Products built on assumptions probably aren’t solving any problems (and might make new issues).
We’ll work on:
- Addressing our own assumptions when we build digital products
- Starting with research & advocating for participatory design
Digital Ageism & Societal Ageism
Digital products have a direct impact on how people are perceived in the real world.
We’ll work on:
- Making age-diversity a starting factor in design, not a last minute check-box
- Considering the implications of tech usage beyond the screen
